0x9F.3 Strix S4
- Nick Kuo
- BSOD Analysis
- 22 Jul, 2024
5: kd> .bugcheck
Bugcheck code 0000009F
Arguments 00000000`00000003 ffff800f`943e4360 ffffc906`fbaa7178 ffff800f`a4a6c7505: kd> !irp ffff800f`a4a6c750
Irp is active with 6 stacks 5 is current (= 0xffff800fa4a6c940)
No Mdl: No System Buffer: Thread 00000000: Irp stack trace.
cmd flg cl Device File Completion-Context
[N/A(0), N/A(0)]
0 0 00000000 00000000 00000000-00000000
Args: 00000000 00000000 00000000 00000000
[N/A(0), N/A(0)]
0 0 00000000 00000000 00000000-00000000
Args: 00000000 00000000 00000000 00000000
[N/A(0), N/A(0)]
0 0 00000000 00000000 00000000-00000000
Args: 00000000 00000000 00000000 00000000
[N/A(0), N/A(0)]
0 0 00000000 00000000 00000000-00000000
Args: 00000000 00000000 00000000 00000000
>[IRP_MJ_POWER(16), IRP_MN_SET_POWER(2)]
0 e1 ffff800f9bfc9030 00000000 fffff8034b12cf80-ffff800fb0e5bcd0 Success Error Cancel pending
\Driver\amduw23g nt!PopRequestCompletion
Args: 00015500 00000001 00000004 00000003
[N/A(0), N/A(0)]
0 0 00000000 00000000 00000000-ffff800fb0e5bcd0
Args: 00000000 00000000 00000000 00000000IRP is going down the stack, running on our stuff. Let’s try to find the thread running it.
I should look for the driver service routine that does IRP_MJ_POWER(16) code, and search the stack.
I forgot the WinDbg function to dump (It’s !drvobj \Driver\amduw23g f), so I’m lazy.
5: kd> !addrMap 0xffff800f`a4a6c750
[INFO] 5 Address maps loaded.
--- Direct Result (Provided address is) ---
Address 0xffff800fa4a6c750 is a value withing a system stack
Found locations:
Address:ffffc907060af280 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 830
Address:ffffc907060af2c0 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 870
Address:ffffc907060af2d8 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 888
Address:ffffc907060af360 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 910
Address:ffffc907060af3a0 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 950
Address:ffffc907060af488 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: a38
Address:ffffc907060af498 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: a48
Address:ffffc907060af520 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: ad0
@$addrMap(0xffff800f`a4a6c750)5: kd> .thread 0xffff800fd3af1580
Implicit thread is now ffff800f`d3af1580
5: kd> k
*** Stack trace for last set context - .thread/.cxr resets it
# Child-SP RetAddr Call Site
00 ffffc907`060aea90 fffff803`4b06c9d5 nt!KiSwapContext+0x76 [minkernel\ntos\ke\amd64\ctxswap.asm @ 134]
01 ffffc907`060aebd0 fffff803`4b06ebb7 nt!KiSwapThread+0xab5 [minkernel\ntos\ke\thredsup.c @ 14700]
02 ffffc907`060aed20 fffff803`4b070ad6 nt!KiCommitThreadWait+0x137 [minkernel\ntos\ke\waitsup.c @ 795]
03 ffffc907`060aedd0 fffff803`4e583646 nt!KeWaitForSingleObject+0x256 [minkernel\ntos\ke\wait.c @ 867]
04 ffffc907`060af170 fffff803`4e583190 dxgkrnl!DpiRequestIoPowerState+0xbe [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 2812]
05 ffffc907`060af210 fffff803`4e582d66 dxgkrnl!DpiFdoSetAdapterPowerState+0x100 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dpfdo.cxx @ 11261]
06 ffffc907`060af2d0 fffff803`4e5827d1 dxgkrnl!DpiFdoHandleDevicePower+0xf6 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 444]
07 ffffc907`060af370 fffff803`4e584200 dxgkrnl!DpiFdoDispatchPower+0x21 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 289]
08 ffffc907`060af3a0 fffff803`4b12dcda dxgkrnl!DpiDispatchPower+0xe0 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dpport.cxx @ 3199]
09 ffffc907`060af4c0 fffff803`4b107167 nt!PopIrpWorker+0x46a [minkernel\ntos\po\irpwork.c @ 608]
0a ffffc907`060af570 fffff803`4b21bb94 nt!PspSystemThreadStartup+0x57 [minkernel\ntos\ps\psexec.c @ 10885]
0b ffffc907`060af5c0 00000000`00000000 nt!KiStartSystemThread+0x34 [minkernel\ntos\ke\amd64\threadbg.asm @ 83]Nice, thread 0xffff800fd3af1580 is doing DpiDispatchPower, this is most likely the 16 routine.
It is waiting for something. Backtrace and identify it is a KEVENT.
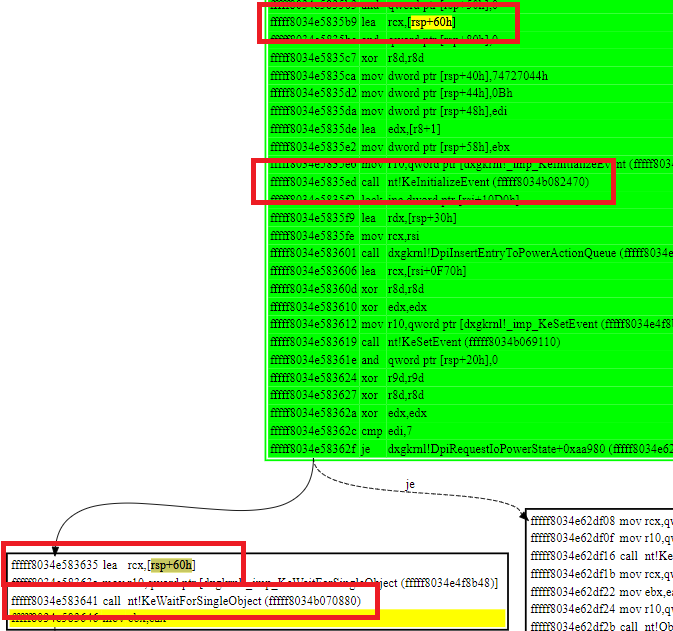
Waiting for KEVENT on RSP+60h. This is passed to dxgkrnl!DpiInsertEntryToPowerActionQueue in 2nd parameter “_DPI_POWER_ACTION” with RSP+30h
Validate by decoding RSP+30 as _DPI_POWER_ACTION
5: kd> dt dxgkrnl!_DPI_POWER_ACTION ffffc907060af170+30
+0x000 ListEntry : _LIST_ENTRY [ 0xffff800f`9bfca110 - 0xffff800f`9bfca110 ]
+0x010 Signature : 0x74727044
+0x014 ContextType : b ( TypePowerActionContext )
+0x018 RequestedPowerAction : 1 ( StateSuspended )
+0x020 Context : (null)
+0x028 Flags : 0x10
+0x030 PowerCompletionEvent : _KEVENT
+0x048 PowerActionStatus : 0n0
+0x050 pScenarioContext : (null)Seems correct, track which list it adds this task to (According to the name DpiInsertEntry… It should insert it into a queue).
The list is in RBX+0F90, RBX is from RCX (_FDO_CONTEXT).
5: kd> dt dxgkrnl!_FDO_CONTEXT 0xffff800f9bfc9180
...
+0xf90 PowerActionQueue : _LIST_ENTRY [ 0xffffc907`060af1a0 - 0xffffc907`060af1a0 ]Let’s try to search for the _FDO_CONTEXT instead.
5: kd> !addrMap 0xffff800f9bfc9180
[INFO] 5 Address maps loaded.
--- Direct Result (Provided address is) ---
Address 0xffff800f9bfc9180 is a DeviceExtension
Owning Device Object: ffff800f9bfc9030
Pool Address: ffff800f9bfc9000
-> Query Device Object: !pnpAddr 0xffff800f9bfc9030
-> Query Pool: !pnpAddr 0xffff800f9bfc9000
--- Indirect Result (Provided address is within) ---
Address 0xffff800f9bfc9000 is a DeviceExtensionPool
Size: 1870
Tag: Devi
Owning Device Extension: ffff800f9bfc9180
-> Query Device Extension: !pnpAddr 0xffff800f9bfc9180
--- Direct Result (Provided address is) ---
Address 0xffff800f9bfc9180 is a value withing a system stack
Found locations:
Address:ffffc906fc997440 Thread 0xffff800f9bfc6100 Thread Id: 940 Stack Offset: ab0
Address:ffffc907060af158 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 708
Address:ffffc907060af200 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 7b0
Address:ffffc907060af228 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 7d8
Address:ffffc907060af278 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 828
Address:ffffc907060af2b8 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 868
Address:ffffc907060af358 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 908
Address:ffffc907060af3a8 Thread 0xffff800fd3af1580 Thread Id: 73904 Stack Offset: 958There is another thread fc6100 that we haven’t seen before. Let’s identify what the thread is doing.
5: kd> !thread 0xffff800f9bfc6100
THREAD ffff800f9bfc6100 Cid 0004.03ac Teb: 0000000000000000 Win32Thread: 0000000000000000 WAIT: (Executive) KernelMode Non-Alertable
ffff800fb2e876b0 SynchronizationEvent
Not impersonating
DeviceMap ffffa103b2e04aa0
Owning Process ffff800f8c12a040 Image: System
Attached Process N/A Image: N/A
Wait Start TickCount 1212752 Ticks: 19434 (0:00:05:03.656)
Context Switch Count 17 IdealProcessor: 3
UserTime 00:00:00.000
KernelTime 00:00:00.000
Win32 Start Address dxgkrnl!DpiPowerArbiterThread (0xfffff8034e5b0fa0)
Stack Init ffffc906fc9975f0 Current ffffc906fc996990
Base ffffc906fc998000 Limit ffffc906fc991000 Call 0000000000000000
Priority 14 BasePriority 8 PriorityDecrement 96 IoPriority 2 PagePriority 5
Child-SP RetAddr : Args to Child : Call Site
ffffc906`fc9969d0 fffff803`4b06c9d5 : ffffcb00`e90a2180 00000000`00000000 ffff800f`8c1cc040 00000000`00000000 : nt!KiSwapContext+0x76 [minkernel\ntos\ke\amd64\ctxswap.asm @ 134]
ffffc906`fc996b10 fffff803`4b06ebb7 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSwapThread+0xab5 [minkernel\ntos\ke\thredsup.c @ 14700]
ffffc906`fc996c60 fffff803`4b070ad6 : 00000000`00000000 ffff800f`00000001 00000000`00000000 00000000`00000000 : nt!KiCommitThreadWait+0x137 [minkernel\ntos\ke\waitsup.c @ 795]
ffffc906`fc996d10 fffff803`45139c39 : ffffc906`fc9972a8 ffffc906`fc9972a8 00000000`00000000 ffff800f`a9a922b8 : nt!KeWaitForSingleObject+0x256 [minkernel\ntos\ke\wait.c @ 867]
ffffc906`fc9970b0 fffff803`4513339e : ffffa103`b3285560 ffffc906`fc997301 00000000`00128101 00000000`00000002 : dxgmms2!VIDMM_GLOBAL::WaitForFences+0x1b9 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 17106]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgmms2!VIDMM_GLOBAL::WaitForFence+0x28 (Inline Function @ fffff803`4513339e) [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\inc\VidMMi.h @ 7612]
ffffc906`fc997200 fffff803`4514dd09 : 00000000`00000001 00000000`c0000030 ffff800f`b0e36000 00000000`ffffef90 : dxgmms2!VIDMM_GLOBAL::QueueSystemCommandAndWaitInternal+0xfe [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9855]
ffffc906`fc997290 fffff803`4514e3b0 : ffff800f`a4b2d010 00000000`ffffff00 00000000`00000002 fffff803`4e581b6c : dxgmms2!VIDMM_GLOBAL::QueueSystemCommandAndWait+0x4d [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9708]
ffffc906`fc9972d0 fffff803`450ba529 : ffff800f`a4b2d010 00000000`00000000 ffff800f`a4b2d010 00000000`00000061 : dxgmms2!VIDMM_GLOBAL::PurgeAllSegments+0xa0 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9539]
ffffc906`fc9973b0 fffff803`4e581ca3 : 00000000`00000000 ffff800f`9a152670 ffffa103`b5dba010 ffffc906`fc997509 : dxgmms2!VidMmPurgeAllSegments+0x9 [onecoreuap\windows\core\dxkernel\dxgkrnl\inc\dxgmms.hxx @ 871]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgkrnl!VIDMM_EXPORT::VidMmPurgeAllSegments+0x21 (Inline Function @ fffff803`4e581ca3) [onecoreuap\windows\core\dxkernel\dxgkrnl\inc\mmsthunk.hxx @ 1583]
ffffc906`fc9973e0 fffff803`4e5b1296 : 00000000`00000061 ffffc906`fc997509 ffff800f`9bfca0c8 ffff800f`9a14c5f0 : dxgkrnl!ADAPTER_RENDER::PurgeSegments+0x9f [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapterrender.cxx @ 3045]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgkrnl!DXGADAPTER::ApplyCoreSyncAction+0xf8 (Inline Function @ fffff803`4e5b1296) [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapter.cxx @ 3802]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgkrnl!DxgkApplyAdapterCoreSyncAction+0xf8 (Inline Function @ fffff803`4e5b1296) [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapterport.cxx @ 471]
ffffc906`fc997450 fffff803`4b107167 : ffff800f`9bfca128 ffff800f`9bfc6100 fffff803`4e5b0fa0 ffff800f`9bfc9030 : dxgkrnl!DpiPowerArbiterThread+0x2f6 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 2109]
ffffc906`fc997570 fffff803`4b21bb94 : ffffcb00`e8b40180 ffff800f`9bfc6100 fffff803`4b107110 00000000`00000000 : nt!PspSystemThreadStartup+0x57 [minkernel\ntos\ps\psexec.c @ 10885]
ffffc906`fc9975c0 00000000`00000000 : ffffc906`fc998000 ffffc906`fc991000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x34 [minkernel\ntos\ke\amd64\threadbg.asm @ 83]It is waiting for a KEVENT. Before we’re sure, take a live machine to inspect who access the list.
Trace the codeflow with live machine
0: kd> .reload /f dxgkrnl.sys
0: kd> bp dxgkrnl!DpiRequestIoPowerState
0: kd> g
Breakpoint 0 hit
dxgkrnl!DpiRequestIoPowerState:
fffff805`5f973588 48895c2408 mov qword ptr [rsp+8],rbx
0: kd> k
# Child-SP RetAddr Call Site
00 ffff9103`aa10f208 fffff805`5f973190 dxgkrnl!DpiRequestIoPowerState [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 2752]
01 ffff9103`aa10f210 fffff805`5f972d66 dxgkrnl!DpiFdoSetAdapterPowerState+0x100 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dpfdo.cxx @ 11261]
02 ffff9103`aa10f2d0 fffff805`5f9727d1 dxgkrnl!DpiFdoHandleDevicePower+0xf6 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 444]
03 ffff9103`aa10f370 fffff805`5f974200 dxgkrnl!DpiFdoDispatchPower+0x21 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 289]
04 ffff9103`aa10f3a0 fffff805`5892dcda dxgkrnl!DpiDispatchPower+0xe0 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dpport.cxx @ 3199]
05 ffff9103`aa10f4c0 fffff805`58907167 nt!PopIrpWorker+0x46a [minkernel\ntos\po\irpwork.c @ 608]
06 ffff9103`aa10f570 fffff805`58a1bb94 nt!PspSystemThreadStartup+0x57 [minkernel\ntos\ps\psexec.c @ 10885]
07 ffff9103`aa10f5c0 00000000`00000000 nt!KiStartSystemThread+0x34 [minkernel\ntos\ke\amd64\threadbg.asm @ 83]
0: kd> t
dxgkrnl!DpiRequestIoPowerState+0x12:
fffff805`5f97359a 488b7140 mov rsi,qword ptr [rcx+40h]
0: kd>
dxgkrnl!DpiRequestIoPowerState+0x18:
fffff805`5f9735a0 33d2 xor edx,edx
0: kd> dt dxgkrnl!_FDO_CONTEXT 0xffffd2028e6bf180
...
+0xf90 PowerActionQueue : _LIST_ENTRY [ 0xffffd202`8e6c0110 - 0xffffd202`8e6c0110 ]
...
0: kd> ba w 8 0xffffd2028e6bf180+0xf90
0: kd> g
Breakpoint 1 hit
dxgkrnl!InsertTailList+0x1c [inlined in dxgkrnl!DpiInsertEntryToPowerActionQueue+0x5a]:
fffff805`5f7af12a 48897b08 mov qword ptr [rbx+8],rdi
0: kd> k
# Child-SP RetAddr Call Site
00 (Inline Function) --------`-------- dxgkrnl!InsertTailList+0x1c [onecore\internal\minwin\priv_sdk\inc\ntrtl_x.h @ 984]
01 ffff9103`aa10f120 fffff805`5f973606 dxgkrnl!DpiInsertEntryToPowerActionQueue+0x5a [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 1774]
02 ffff9103`aa10f170 fffff805`5f973190 dxgkrnl!DpiRequestIoPowerState+0x7e [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 2793]
03 ffff9103`aa10f210 fffff805`5f972d66 dxgkrnl!DpiFdoSetAdapterPowerState+0x100 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dpfdo.cxx @ 11261]
04 ffff9103`aa10f2d0 fffff805`5f9727d1 dxgkrnl!DpiFdoHandleDevicePower+0xf6 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 444]
05 ffff9103`aa10f370 fffff805`5f974200 dxgkrnl!DpiFdoDispatchPower+0x21 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 289]
06 ffff9103`aa10f3a0 fffff805`5892dcda dxgkrnl!DpiDispatchPower+0xe0 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dpport.cxx @ 3199]
07 ffff9103`aa10f4c0 fffff805`58907167 nt!PopIrpWorker+0x46a [minkernel\ntos\po\irpwork.c @ 608]
08 ffff9103`aa10f570 fffff805`58a1bb94 nt!PspSystemThreadStartup+0x57 [minkernel\ntos\ps\psexec.c @ 10885]
09 ffff9103`aa10f5c0 00000000`00000000 nt!KiStartSystemThread+0x34 [minkernel\ntos\ke\amd64\threadbg.asm @ 83]
0: kd> g
Breakpoint 1 hit
dxgkrnl!RemoveHeadList+0x15 [inlined in dxgkrnl!DpiGetPowerActionQueueEntry+0x5a]:
fffff805`5f7b015a 48895808 mov qword ptr [rax+8],rbx
4: kd> k
# Child-SP RetAddr Call Site
00 (Inline Function) --------`-------- dxgkrnl!RemoveHeadList+0x15 [onecore\internal\minwin\priv_sdk\inc\ntrtl_x.h @ 923]
01 ffff9103`a2b57400 fffff805`5f9a1024 dxgkrnl!DpiGetPowerActionQueueEntry+0x5a [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 1742]
02 ffff9103`a2b57450 fffff805`58907167 dxgkrnl!DpiPowerArbiterThread+0x84 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 1954]
03 ffff9103`a2b57570 fffff805`58a1bb94 nt!PspSystemThreadStartup+0x57 [minkernel\ntos\ps\psexec.c @ 10885]
04 ffff9103`a2b575c0 00000000`00000000 nt!KiStartSystemThread+0x34 [minkernel\ntos\ke\amd64\threadbg.asm @ 83]So we should be on the right path, DpiPowerArbiterThread is responsible for dequeuing the list and process the work inside. In our dump it corresponds to the stuck thread fc6100.
Thread fc6100 is waiting for a KEVENT. Identify it.
5: kd> !thread 0xffff800f9bfc6100
THREAD ffff800f9bfc6100 Cid 0004.03ac Teb: 0000000000000000 Win32Thread: 0000000000000000 WAIT: (Executive) KernelMode Non-Alertable
ffff800fb2e876b0 SynchronizationEvent
Not impersonating
DeviceMap ffffa103b2e04aa0
Owning Process ffff800f8c12a040 Image: System
Attached Process N/A Image: N/A
Wait Start TickCount 1212752 Ticks: 19434 (0:00:05:03.656)
Context Switch Count 17 IdealProcessor: 3
UserTime 00:00:00.000
KernelTime 00:00:00.000
Win32 Start Address dxgkrnl!DpiPowerArbiterThread (0xfffff8034e5b0fa0)
Stack Init ffffc906fc9975f0 Current ffffc906fc996990
Base ffffc906fc998000 Limit ffffc906fc991000 Call 0000000000000000
Priority 14 BasePriority 8 PriorityDecrement 96 IoPriority 2 PagePriority 5
Child-SP RetAddr : Args to Child : Call Site
ffffc906`fc9969d0 fffff803`4b06c9d5 : ffffcb00`e90a2180 00000000`00000000 ffff800f`8c1cc040 00000000`00000000 : nt!KiSwapContext+0x76 [minkernel\ntos\ke\amd64\ctxswap.asm @ 134]
ffffc906`fc996b10 fffff803`4b06ebb7 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSwapThread+0xab5 [minkernel\ntos\ke\thredsup.c @ 14700]
ffffc906`fc996c60 fffff803`4b070ad6 : 00000000`00000000 ffff800f`00000001 00000000`00000000 00000000`00000000 : nt!KiCommitThreadWait+0x137 [minkernel\ntos\ke\waitsup.c @ 795]
ffffc906`fc996d10 fffff803`45139c39 : ffffc906`fc9972a8 ffffc906`fc9972a8 00000000`00000000 ffff800f`a9a922b8 : nt!KeWaitForSingleObject+0x256 [minkernel\ntos\ke\wait.c @ 867]
ffffc906`fc9970b0 fffff803`4513339e : ffffa103`b3285560 ffffc906`fc997301 00000000`00128101 00000000`00000002 : dxgmms2!VIDMM_GLOBAL::WaitForFences+0x1b9 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 17106]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgmms2!VIDMM_GLOBAL::WaitForFence+0x28 (Inline Function @ fffff803`4513339e) [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\inc\VidMMi.h @ 7612]
ffffc906`fc997200 fffff803`4514dd09 : 00000000`00000001 00000000`c0000030 ffff800f`b0e36000 00000000`ffffef90 : dxgmms2!VIDMM_GLOBAL::QueueSystemCommandAndWaitInternal+0xfe [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9855]
ffffc906`fc997290 fffff803`4514e3b0 : ffff800f`a4b2d010 00000000`ffffff00 00000000`00000002 fffff803`4e581b6c : dxgmms2!VIDMM_GLOBAL::QueueSystemCommandAndWait+0x4d [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9708]
ffffc906`fc9972d0 fffff803`450ba529 : ffff800f`a4b2d010 00000000`00000000 ffff800f`a4b2d010 00000000`00000061 : dxgmms2!VIDMM_GLOBAL::PurgeAllSegments+0xa0 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9539]
ffffc906`fc9973b0 fffff803`4e581ca3 : 00000000`00000000 ffff800f`9a152670 ffffa103`b5dba010 ffffc906`fc997509 : dxgmms2!VidMmPurgeAllSegments+0x9 [onecoreuap\windows\core\dxkernel\dxgkrnl\inc\dxgmms.hxx @ 871]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgkrnl!VIDMM_EXPORT::VidMmPurgeAllSegments+0x21 (Inline Function @ fffff803`4e581ca3) [onecoreuap\windows\core\dxkernel\dxgkrnl\inc\mmsthunk.hxx @ 1583]
ffffc906`fc9973e0 fffff803`4e5b1296 : 00000000`00000061 ffffc906`fc997509 ffff800f`9bfca0c8 ffff800f`9a14c5f0 : dxgkrnl!ADAPTER_RENDER::PurgeSegments+0x9f [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapterrender.cxx @ 3045]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgkrnl!DXGADAPTER::ApplyCoreSyncAction+0xf8 (Inline Function @ fffff803`4e5b1296) [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapter.cxx @ 3802]
(Inline Function) --------`-------- : --------`-------- --------`-------- --------`-------- --------`-------- : dxgkrnl!DxgkApplyAdapterCoreSyncAction+0xf8 (Inline Function @ fffff803`4e5b1296) [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapterport.cxx @ 471]
ffffc906`fc997450 fffff803`4b107167 : ffff800f`9bfca128 ffff800f`9bfc6100 fffff803`4e5b0fa0 ffff800f`9bfc9030 : dxgkrnl!DpiPowerArbiterThread+0x2f6 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dppower.cxx @ 2109]
ffffc906`fc997570 fffff803`4b21bb94 : ffffcb00`e8b40180 ffff800f`9bfc6100 fffff803`4b107110 00000000`00000000 : nt!PspSystemThreadStartup+0x57 [minkernel\ntos\ps\psexec.c @ 10885]
ffffc906`fc9975c0 00000000`00000000 : ffffc906`fc998000 ffffc906`fc991000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x34 [minkernel\ntos\ke\amd64\threadbg.asm @ 83]in dxgmms2!VIDMM_GLOBAL::WaitForFences, it waits for an event in RSP+50h.
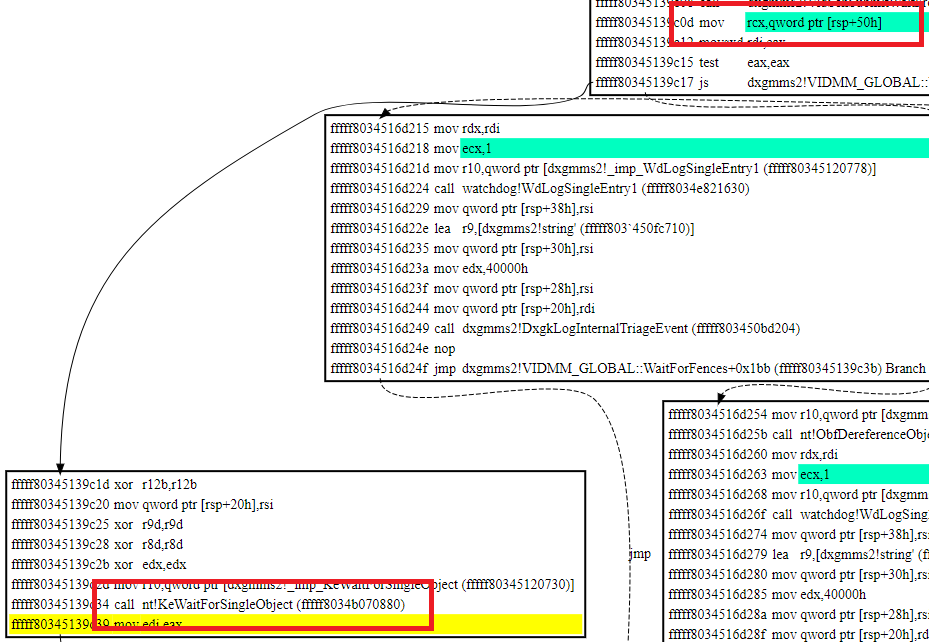
All the way in the beginning of the routine, we see RSP+50 is set to RDX. There’s no branch setting it to other values.
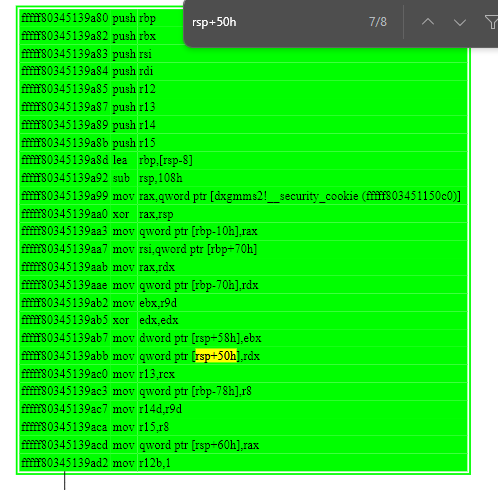
5: kd> x dxgmms2!VIDMM_GLOBAL::WaitForFences
fffff803`45139a80 dxgmms2!VIDMM_GLOBAL::WaitForFences (struct _VIDSCH_SYNC_OBJECT **, unsigned int64 *, unsigned int, unsigned int64 *)RDX does not have a type, let’s keep tracing upwards. Came from LEA RBP-20, which has value of R15. R15 came from R9.
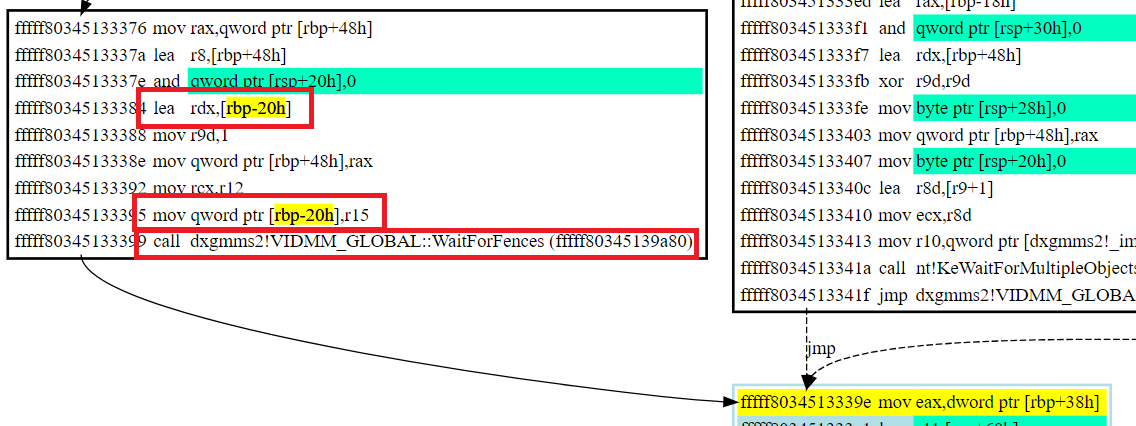
I give up. Used a live machine to inspect. It came from a DPC in our driver.
16: kd> ub dxgmms2!VIDMM_GLOBAL::WaitForFences+0x1b9
dxgmms2!VIDMM_GLOBAL::WaitForFences+0x197 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 17092]:
fffff805`59dd9c17 0f8837360300 js dxgmms2!VIDMM_GLOBAL::WaitForFences+0x337d4 (fffff805`59e0d254)
fffff805`59dd9c1d 4532e4 xor r12b,r12b
fffff805`59dd9c20 4889742420 mov qword ptr [rsp+20h],rsi
fffff805`59dd9c25 4533c9 xor r9d,r9d
fffff805`59dd9c28 4533c0 xor r8d,r8d
fffff805`59dd9c2b 33d2 xor edx,edx
fffff805`59dd9c2d 4c8b15fc6afeff mov r10,qword ptr [dxgmms2!_imp_KeWaitForSingleObject (fffff805`59dc0730)]
fffff805`59dd9c34 e8476ca9fe call nt!KeWaitForSingleObject (fffff805`58870880)
16: kd> bp fffff805`59dd9c34
16: kd> g
Breakpoint 1 hit
dxgmms2!VIDMM_GLOBAL::WaitForFences+0x1b4:
fffff805`59dd9c34 e8476ca9fe call nt!KeWaitForSingleObject (fffff805`58870880)
1: kd> k
# Child-SP RetAddr Call Site
00 ffff9103`a7f16ca0 fffff805`59dd339e dxgmms2!VIDMM_GLOBAL::WaitForFences+0x1b4 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 17106]
01 (Inline Function) --------`-------- dxgmms2!VIDMM_GLOBAL::WaitForFence+0x28 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\inc\VidMMi.h @ 7612]
02 ffff9103`a7f16df0 fffff805`59ddaafc dxgmms2!VIDMM_GLOBAL::QueueSystemCommandAndWaitInternal+0xfe [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9855]
03 (Inline Function) --------`-------- dxgmms2!VIDMM_GLOBAL::QueueSystemCleanupCommandAndWait+0x54 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 9723]
04 ffff9103`a7f16e80 fffff805`59dd05f7 dxgmms2!VIDMM_GLOBAL::CloseOneAllocation+0x1ac [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 5272]
05 ffff9103`a7f16fd0 fffff805`59d4268a dxgmms2!VIDMM_GLOBAL::CloseAllocation+0xc3 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidmm\mmglobal.cxx @ 5039]
06 ffff9103`a7f17020 fffff805`5f93c3ea dxgmms2!VidMmCloseAllocation+0x1a [onecoreuap\windows\core\dxkernel\dxgkrnl\inc\dxgmms.hxx @ 1144]
07 (Inline Function) --------`-------- dxgkrnl!VIDMM_EXPORT::VidMmCloseAllocation+0x25 [onecoreuap\windows\core\dxkernel\dxgkrnl\inc\mmsthunk.hxx @ 1769]
08 ffff9103`a7f17060 fffff805`5f93c143 dxgkrnl!DXGDEVICE::DestroyDeferredAllocations+0xca [onecoreuap\windows\core\dxkernel\dxgkrnl\core\alloc.cxx @ 1857]
09 (Inline Function) --------`-------- dxgkrnl!ADAPTER_RENDER::DeferredDestructionWork+0x7c [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapterrender.cxx @ 4535]
0a ffff9103`a7f172e0 fffff805`58834f85 dxgkrnl!DxgkpDeferredDestructionWork+0xa3 [onecoreuap\windows\core\dxkernel\dxgkrnl\core\adapterpublic.cxx @ 9546]
0b ffff9103`a7f17380 fffff805`58907167 nt!ExpWorkerThread+0x155 [minkernel\ntos\ex\worker.c @ 4308]
0c ffff9103`a7f17570 fffff805`58a1bb94 nt!PspSystemThreadStartup+0x57 [minkernel\ntos\ps\psexec.c @ 10885]
0d ffff9103`a7f175c0 00000000`00000000 nt!KiStartSystemThread+0x34 [minkernel\ntos\ke\amd64\threadbg.asm @ 83]
1: kd> r
rax=0000000000000000 rbx=ffff9103a7f16e98 rcx=ffffd202aba7cee0
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80559dd9c34 rsp=ffff9103a7f16ca0 rbp=ffff9103a7f16da0
r8=0000000000000000 r9=0000000000000000 r10=fffff80558870880
r11=ffff9103a7f16c80 r12=ffffd202a3b8b000 r13=ffffd202a3b8b000
r14=0000000000000001 r15=ffff9103a7f16e98
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040246
dxgmms2!VIDMM_GLOBAL::WaitForFences+0x1b4:
fffff805`59dd9c34 e8476ca9fe call nt!KeWaitForSingleObject (fffff805`58870880)
1: kd> ba w 0x8 ffffd202aba7cee0
1: kd> g
Breakpoint 3 hit
nt!KiAcquireKobjectLockSafe+0x14:
fffff805`588e3db4 720c jb nt!KiAcquireKobjectLockSafe+0x22 (fffff805`588e3dc2)
15: kd> k
# Child-SP RetAddr Call Site
00 ffff9103`a1b8ed40 fffff805`5886917b nt!KiAcquireKobjectLockSafe+0x14 [minkernel\ntos\ke\waitsup.c @ 3230]
01 (Inline Function) --------`-------- nt!KiAcquireKobjectLock+0xd [minkernel\ntos\ke\waitsup.c @ 3266]
02 ffff9103`a1b8ed70 fffff805`59d43f51 nt!KeSetEvent+0x6b [minkernel\ntos\ke\eventobj.c @ 412]
03 ffff9103`a1b8ee00 fffff805`59d43d0e dxgmms2!VidSchiUnwaitMonitoredFences+0x171 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 26392]
04 ffff9103`a1b8eed0 fffff805`59d46a33 dxgmms2!VidSchiCompleteSignalSyncObject+0x8e [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 26697]
05 (Inline Function) --------`-------- dxgmms2!VidSchiCompleteSignalCommmand+0x6c [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 26779]
06 ffff9103`a1b8ef30 fffff805`59d467c8 dxgmms2!VidSchiProcessCompletedQueuePacketInternal+0x1f3 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 13786]
07 (Inline Function) --------`-------- dxgmms2!VidSchiProcessCompletedQueuePacket+0x8 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 14193]
08 ffff9103`a1b8f100 fffff805`59d4ba6c dxgmms2!VidSchiProcessDpcCompletedPacket+0x1108 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 12351]
09 ffff9103`a1b8f290 fffff805`59d4ac3e dxgmms2!VidSchiProcessDpcDmaPacket+0xdc [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 11478]
0a (Inline Function) --------`-------- dxgmms2!VidSchDdiNotifyDpcWorker+0x90 [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 9207]
0b ffff9103`a1b8f320 fffff805`5f7a31b9 dxgmms2!VidSchDdiNotifyDpc+0x15e [onecoreuap\windows\core\dxkernel\dxgkrnl\dxgmms2\vidsch\vidschi.cxx @ 9114]
0c (Inline Function) --------`-------- dxgkrnl!VIDSCH_EXPORT::VidSchDdiNotifyDpc+0x17 [onecoreuap\windows\core\dxkernel\dxgkrnl\inc\mmsthunk.hxx @ 68]
0d ffff9103`a1b8f390 fffff805`b39e1b01 dxgkrnl!DxgNotifyDpcCB+0x99 [onecoreuap\windows\core\dxkernel\dxgkrnl\core\corethnk.cxx @ 99]
0e ffff9103`a1b8f470 fffff805`b3b2dceb amdkmdag!InterruptManager::NotifyDPC+0x51 [c:\constructicon\builds\gfx\one\23.40\drivers\kmd\src\InterruptManager.cpp @ 7196]
0f ffff9103`a1b8f4d0 fffff805`b3b359b2 amdkmdag!FeatureMgr::DdiDpcRoutine+0x10b [c:\constructicon\builds\gfx\one\23.40\drivers\kmd\features\FeatureMgr.cpp @ 3478]
10 ffff9103`a1b8f500 fffff805`b3bd500c amdkmdag!FeatureMgr::GpuInt_DpcCallback+0x52 [c:\constructicon\builds\gfx\one\23.40\drivers\kmd\features\FeatureMgr.cpp @ 3848]
11 ffff9103`a1b8f5a0 fffff805`b3bd7bc8 amdkmdag!DoDeferredCallback+0x98 [c:\constructicon\builds\gfx\one\23.40\drivers\irqmgr\src\callback.c @ 151]
12 ffff9103`a1b8f5d0 fffff805`b3bd7621 amdkmdag!MediumPriorityQueue_ProcessWorkItem+0x140 [c:\constructicon\builds\gfx\one\23.40\drivers\irqmgr\src\medium_priority_queue.c @ 423]
13 ffff9103`a1b8f640 fffff805`b3bd1dfa amdkmdag!MediumPriorityQueue_DpcRoutine+0x75 [c:\constructicon\builds\gfx\one\23.40\drivers\irqmgr\src\medium_priority_queue.c @ 255]
14 ffff9103`a1b8f6e0 fffff805`b39d96ca amdkmdag!IRQMGR_DpcRoutine+0xe [c:\constructicon\builds\gfx\one\23.40\drivers\irqmgr\src\irqmgr.c @ 408]
15 ffff9103`a1b8f710 fffff805`b3a7e1cb amdkmdag!AtiDpc+0xba [c:\constructicon\builds\gfx\one\23.40\drivers\kmd\src\InterruptManager.cpp @ 4133]
16 ffff9103`a1b8f740 fffff805`5f7a4b75 amdkmdag!ProxyDpcRoutine+0x4b [c:\constructicon\builds\gfx\one\23.40\drivers\pxproxy\kmd\ddi.cpp @ 910]
17 ffff9103`a1b8f770 fffff805`5887148c dxgkrnl!DpiFdoDpcForIsr+0x75 [onecoreuap\windows\core\dxkernel\dxgkrnl\port\dpfdo.cxx @ 4605]
18 ffff9103`a1b8f7c0 fffff805`58872741 nt!KiExecuteAllDpcs+0x42c [minkernel\ntos\ke\dpcsup.c @ 2717]
19 ffff9103`a1b8fd00 fffff805`58a20135 nt!KiRetireDpcList+0x1b1 [minkernel\ntos\ke\dpcsup.c @ 3175]
1a ffff9103`a1b8ffb0 fffff805`58a200df nt!KySwapStacksAndRetireDpcList+0x5 [minkernel\ntos\ke\amd64\platform.asm @ 279]
1b ffff9103`a6a86360 fffff805`588609d5 nt!KiPlatformSwapStacksAndCallReturn [minkernel\ntos\ke\amd64\platform.asm @ 102]
1c ffff9103`a6a86370 fffff805`58a1f89b nt!KiDispatchInterrupt+0xd5 [minkernel\ntos\ke\dispatchint.c @ 128]
1d ffff9103`a6a86460 fffff805`58a18d81 nt!KiDpcInterruptBypass+0x1b [minkernel\ntos\ke\amd64\dpcint.asm @ 183]
1e ffff9103`a6a86490 fffff805`5e1934ad nt!KiInterruptDispatch+0xb1 [minkernel\ntos\ke\amd64\intsup.asm @ 613]
... Not important stuff ...Bruh… It came from a driver DPC notify.
Summary
- Thread 0xffff800fd3af1580
- Running dxgkrnl!DpiDispatchPower (IRP_MJ_POWER handler)
- Queue a _DPI_POWER_ACTION for DpiPowerArbiterThread to process
- Waiting for _DPI_POWER_ACTION.PowerCompletionEvent
- Thread 0xffff800f9bfc6100
- Running dxgkrnl!DpiPowerArbiterThread
- Calls dxgmms2!VIDMM_GLOBAL::QueueSystemCommandAndWait
- Calls dxgmms2!VIDMM_GLOBAL::WaitForFences
- Waits for a “fence”
- A fence is returned by a DPC.
- In dump, this likely didn’t happen.